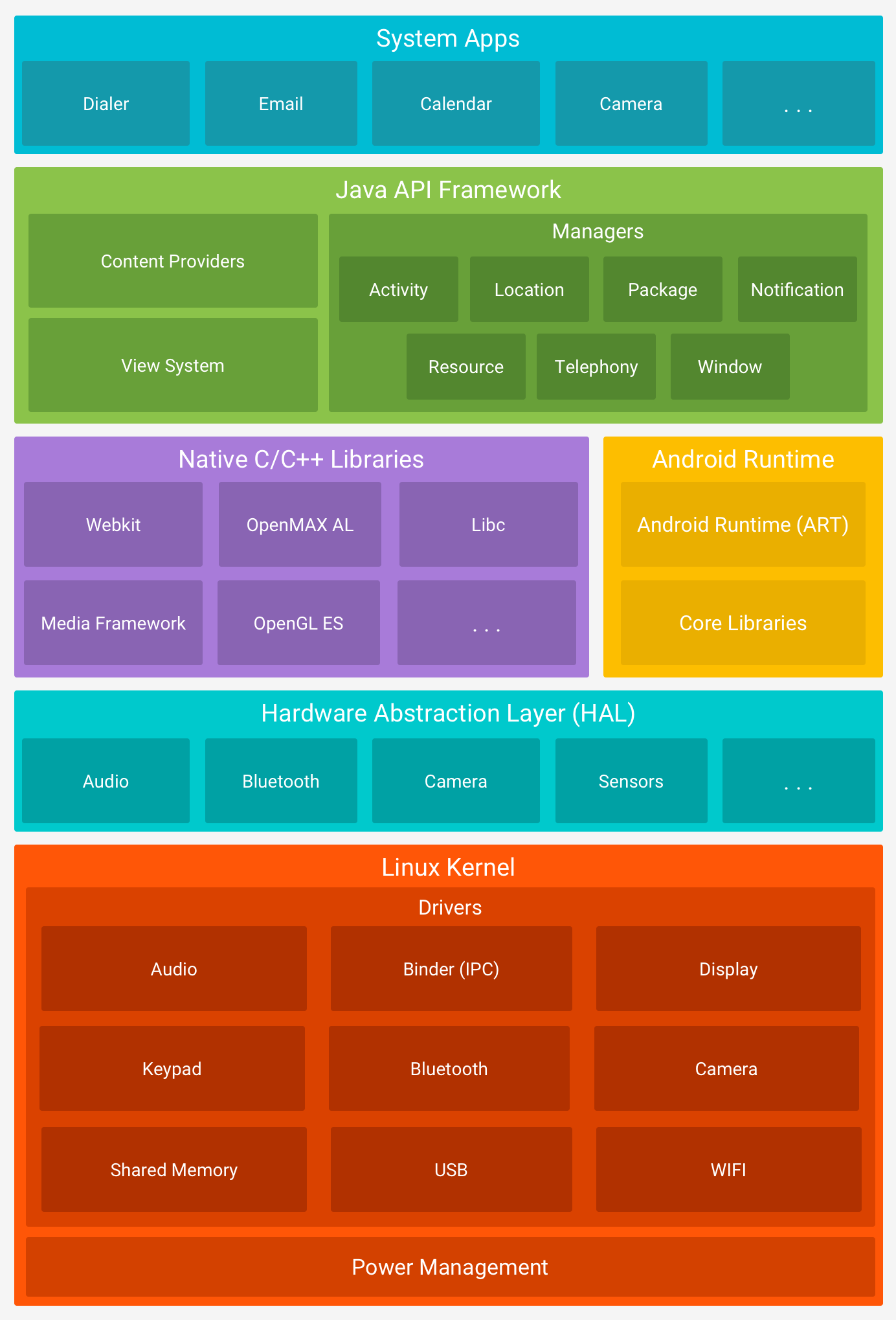
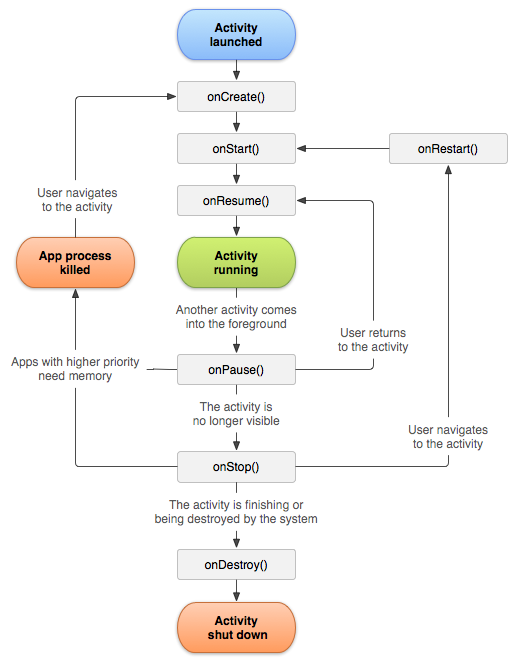
I’ve been using android since I was 10 years old. I have seen the growth of android. I used to have this Beetel tablet. And If I remember correctly, There was no PlayStore, it was just Market. The application name where we could buy and install the apps was called Market (Green Icon). I was not a security geek back then but now that I am right now, I understand the working of an android device. because I have seen the changes (well, not the names) in android. The features, security, bugs, bugs in the features, and then again the security to prevent those bugs in the features. I won’t lie but Android systems are quite complex. Think of it like this, we are using a Linux system and for some people it is complex. well, android systems are totally based on Linux systems. by that, what I mean is there are more layers over Linux to run an application and services.
every time I see this image, I am always amazed to see how fast the android works even though there are so many layers. we are going to do some basic of Frida, Jadx and Genymotion. basically, this article is a mix-up of setting up an android emulator, reverse engineering APKs and android debugging.
The first and obvious thing would be an android system so that we may run our applications. The best emulator for testing purposes is Genymotion. you must have heard about it because almost all bug hunters use this to find bugs in android applications. The best thing I found about this is that you can run any android version with customization.


You can download this from here and install it on your system. I have downloaded it on another windows system and I have forwarded port 5555 (ADB port) using netsh command.
netsh interface portproxy add v4tov4 listenaddress=<Genymotion android IP> listenport=5555 connectaddress=0.0.0.0.0 connectport=5555Just make sure you type the correct IP in listenaddress. the default port for ADB service is always 5555. and keep one thing in mind, we are only doing this for IPv4 which means the socket address we are forming with port 5555 is for IPv4. so, you can’t connect it with IPv6. by the way, you won’t even need to run this command, I am using a Windows system to run Genymotion and the main system to run Linux That’s what made me use this netsh command.
After that, you can easily connect with the adb service.
adb connect <IP:5555>
adb devices now that you are connected to the ADB service, you can get the shell of the system and literally do whatever you want.
I can list out the packages installed on my device.

To know the path of a package, you can use the following command:
vbox86p:/ # pm path com.amaze.filemanager
package:/system/app/Amaze/Amaze.apk
you can even run an application from the ADB shell. To do so you will need to know the package name and the activity (intent) in that package. I have already told you the way to find packages in android using ADB. all we need is actions for a package. there are many ways to enumerate actions but the one I find simple is with the command `aapt`. you can install it using apt package manager in Kali Linux.
apt install aaptthen you can run a dump on an apk to extract the activities.
08:22:59 root@gojoker level_2 → aapt dump badging UnCrackable-Level2.apk | grep -i activity
launchable-activity: name='sg.vantagepoint.uncrackable2.MainActivity' label='' icon=''
So for example, I have this app installed `UnCrackable-Level2.apk` and the starting activity I have found is `sg.vantagepoint.uncrackable2.MainActivity`.
There is a command which you can use to start an activity. you will do this using the ADB shell and the activity will show up on the actual android emulator.
vbox86p:/tmp # am start owasp.mstg.uncrackable2/sg.vantagepoint.uncrackable2.MainActivity
Starting: Intent { act=android.intent.action.MAIN cat=[android.intent.category.LAUNCHER] cmp=owasp.mstg.uncrackable2/sg.vantagepoint.uncrackable2.MainActivity }
now that we know little basics of android emulator and ADB. we should move on to a debugger & decompiler JADX. I am using jadx-gui which I like more than the CLI version. you can download it from GitHub and build it.
10:03:08 root@gojoker jadx ±|master|→ ./gradlew dist
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Downloading https://services.gradle.org/distributions/gradle-7.5.1-bin.zip
...........10%............20%...........30%............40%...........50%............60%...........70%............80%...........90%............100%
Welcome to Gradle 7.5.1!
Here are the highlights of this release:
- Support for Java 18
- Support for building with Groovy 4
- Much more responsive continuous builds
- Improved diagnostics for dependency resolution
For more details see https://docs.gradle.org/7.5.1/release-notes.html
Starting a Gradle Daemon (subsequent builds will be faster)
<-------------> 0% CONFIGURING [2s]
> Building buildSrc
....build/jadx/bin/jadx-gui# run itYou can decompile `apk, dex, class, aar, jadx etc` files. for demonstration, I am using uncrackable2 apk. you can download this or even use another apk file.

The first thing we do is see the AndroidManifeast.xml file in Resources because this file gives you the brief of the apk. you can view the permissions and activities available in the apk.
we can read the source code for an activity. for example the activity we found in the AndroidManifeast.xml file (sg.vantagepoint.uncrackable2.MainActivity).

There is a button (green bug icon) on the top bar of jadx-gui. you can use it to start debugging the application. but it requires the ADB service to have one or more devices to run the application on that.
To start debugging, click on it, and start the ADB server if you haven’t already then you should see the devices and processes on the devices. then you will press `launch app` to start the process of the app that you want to debug then double-click on that newly created process.
 Then you do what you do while debugging any other program in vscode or in pycharm.
Then you do what you do while debugging any other program in vscode or in pycharm.
One more thing is left and this is quite complex. this is an android debugging framework `Frida`. it is complex because to use this, you have to understand Javascript, Java (App development) and Python (Not necessary). well, I don’t understand this framework at all but I’ll try my best to give a brief introduction to this framework.
It’s Greasemonkey for native apps, or, put in more technical terms, it’s a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript or your own library into native apps on Windows, macOS, GNU/Linux, iOS, Android, and QNX. Frida also provides you with some simple tools built on top of the Frida API. These can be used as-is, tweaked to your needs, or serve as examples of how to use the API.
you can install it using the pip command:
pip install frida-toolsThis command installs some Frida tools which include:
frida-apk frida-compile frida-create frida-discover frida-join frida-kill frida-ls frida-ls-devices frida-ps frida-pull frida-push frida-rm frida-traceI will not describe all of these tools but only the ones I have used and found necessary. The first step is to run the frida-server in android. so that we can interact with android processes. it is an injection mode of Frida. and believe me, you don’t wanna get into the operation modes of Frida. just keep one thing in mind, we use injection mode when the device is jailbroken or rooted. by the way, genymotion creates a rooted device by default so that won’t be a problem.
You can download this binary for genymotion: click here
xz -d frida-server-16.0.1-linux-x86.xz
adb push ./frida-server-16.0.1-linux-x86 /tmp
adb shell chmod +x /tmp/frida-server-16.0.1-linux-x86
adb shell /tmp/frida-server-16.0.1-linux-x86It should run the frida-server in your android device(rooted). now you can use other frida tools (as clients). you can view the processes in the android using frida-ps command.
07:40:26 root@gojoker Downloads → frida-ps -U
PID Name
----- ------------------------------
1498 Android Security Testing
1343 Calendar
14998 Clock
1378 Email
21314 Search
781 Settings
136 adbd
984 android.ext.services
1258 android.process.acore
268 audioserver
258 batteryd
269 cameraserver
665 com.android.inputmethod.latin
1122 com.android.launcher3
767 com.android.phone
1035 com.android.printspooler
1365 com.android.providers.calendar
...The only flag you need to remember is `-U` because if you don’t supply this, Frida is gonna perform the task for your own system.
To list all the running and installed apps:
07:50:42 root@gojoker level_2 → frida-ps -U -ai
PID Name Identifier
----- --------------------------- --------------------------------
1498 Android Security Testing hpandro.android.security
1343 Calendar com.android.calendar
14998 Clock com.android.deskclock
1378 Email com.android.email
21314 Search com.android.quicksearchbox
781 Settings com.android.settings
- API Demos com.example.android.apis
- Amaze com.amaze.filemanager
- Calculator com.android.calculator2
- Camera com.android.camera2
- Contacts com.android.contacts
- Custom Locale com.android.customlocale2
- Dev Tools com.android.development
- Development Settings com.android.development_settings
- Files com.android.documentsui
- Gallery com.android.gallery3d
- Messaging com.android.messaging
- Music com.android.music
- Phone com.android.dialer
- Superuser com.genymotion.superuser
- Uncrackable Level 2 owasp.mstg.uncrackable2
- WebView Shell org.chromium.webview_shell
- com.android.gesture.builder com.android.gesture.builder
The next thing we can do is attach a process to Frida or start a new process using package name.
08:08:38 root@gojoker level_2 → frida -U -p 1498
____
/ _ | Frida 15.2.2 - A world-class dynamic instrumentation toolkit
| (_| |
> _ | Commands:
/_/ |_| help -> Displays the help system
. . . . object? -> Display information about 'object'
. . . . exit/quit -> Exit
. . . .
. . . . More info at https://frida.re/docs/home/
. . . .
. . . . Connected to Google (id=192.168.12.190:5555)
[Google::PID::1498 ]-> now it is all about how much you know Javascript and Java. This is an interpreter just like Python, bash or Ruby. you can perform arithmetic operations here. you can even print some strings with console.log() function. There is a Java object you could use in many ways. before going to use it, there is a concept of the Android activity lifecycle. Maybe the android developers are already aware of it. there are some methods which are used when an activity is created, deleted, suspended etc.
for example, I want my application(activity) to look for notifications (request the server) when the application is started (onCreate). and I want my application to kill all the child processes it may have created while the process ends (onDestroy). If I go back into the jadx-gui output and view the MainActivity source, I can easily spot these methods.
I am explaining this because I wanted to show you the power of Frida. Frida can overwrite any method in any class. I am calling a function just for demonstration. The method is `m2a` but the actual name of this function is `a`. I don’t know how this naming conversion works in jadx.
frida -U -f owasp.mstg.uncrackable2Java.perform(function(){Java.use("sg.vantagepoint.uncrackable2.MainActivity").a.overload("java.lang.String").implementation = function(str) {this.a("KINGPINGAAAAAAAAAAAAA")};})Insert this script into Frida’s interpreter. and you should see something like this:
These are some links which will guide you more about what just happened here:
1. https://neo-geo2.gitbook.io/adventures-on-security/frida-scripting-guide/methods
2. https://nibarius.github.io/learning-frida/2020/05/16/uncrackable1
3. https://medium.com/android-news/hacking-android-app-with-frida-a85516f4f8b7